Understanding the Nintendo Switch secure boot vulnerabilities
 A public domain image of the Switch from Wikipedia
A public domain image of the Switch from Wikipedia
Problem statement
I wanted to understand the security vulnerabilities that allow people to run custom firmware (or Linux) on the Nintendo Switch1.
There are many reasons why one would want to run custom firmware on the console. They range from customization (my Switch looks way different than any other Switch), through unlocking (or even implementing) additional features that aren’t typically available… and all the way to game piracy.
For me the main interest is academical, but wouldn’t it be nice to be able to use a single SD card instead of all of the following2?
 a very partial collection of our games
a very partial collection of our games
Meaning that I’m more interested in understanding the technical details (how it’s done) than in actually using it.
Option one: Really old firmware
There were several software-only bugs found in older firmwares (Nereba for 1.0.0, Caffeine for 2.0.0-4.1.0), which I’m declaring out of scope.
Option two: Unpatched V1 Switch (Erista)
This option is interesting in its seeming simplicity – for the end user – and the awesome amount of work it took to discover.
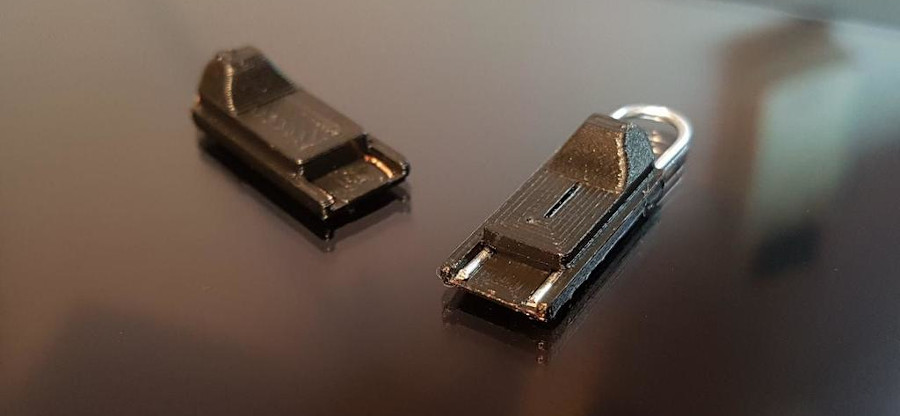 3d printed “RCM jig” by MakeTo3D
3d printed “RCM jig” by MakeTo3D
On a high level, powering on the console while shorting two Joycon pins (using an “RCM jig” or a bent hairpin) and holding volume up, will make the Switch enter a recovery mode (RCM). Which is normally supposed to accept RSA-signed RCM payload to boot from.
But, the unpatched Switches have a buffer overflow vulnerability in the recovery mode implementation:
To gently scratch the surface, an attacker initiates a USB bulk transfer (to
upload the RCM payload) and before finishing the transfer issues a GET_STATUS
USB control transfer with an oversized size field. The control transfer
implementation is missing a bounds check, which causes it to overwrite not only
the entire DMA buffer but also stack… with data from the pending bulk transfer.
Profit.
All the details of how this was found and eventually exploited are nicely explained in the Glitching the Switch presentation by Andreas Galauner. Or in the Vulnerability Disclosure: Fusée Gelée paper.
In any case, the funny thing is – since this vulnerability is burned into the BootROM of the vulnerable Switches, there’s nothing anyone can do about it. They are vulnerable forever.
Option three: modchips for the V1/V2/OLED Switches (Erista, Mariko, Aula)
Modchips have a long tradition in consoles3. So after Nvidia fixed the Tegra X1 BootROM vulnerability and Nintendo the firmware bugs, modchips are basically the only realistic way to get custom firmware running.
I won’t go into the legality of this, the arrests of Team Xecuter, etc. Rather, let’s talk a bit about how the Switch modchip works4.
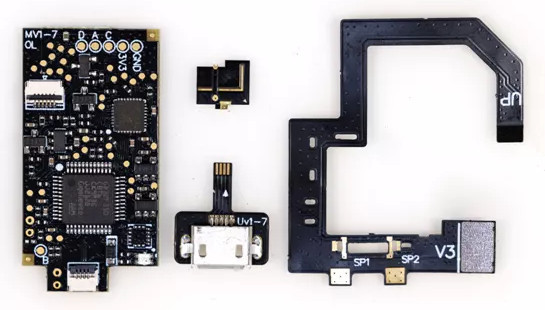 Switch modchip supposedly compatible with all versions
Switch modchip supposedly compatible with all versions
There are four pieces to it (left to right):
- Board
- eMMC
DAT0adapter - micro-USB adapter – to update modchip’s MCU firmware
- CPU strap
The board has two main components: a GD32 MCU (the big chip in the bottom center) and an ICE40 FPGA (the small chip in the top right).
The CPU strap (on the right) sports N-channel mosfets (NP2016) on its underside.
On a high level, it gets soldered into the Switch to its:
DAT0,CLK,CMDlines from the eMMCRST,3v3andGNDlines- CPU bypass caps
And the mechanism of action, as far as I could find out (so far):
- Rewrite
BOOT0region on the eMMC with intended boot code (Spacecraft-NX) - Power-glitch the Tegra X1 to skip the signature check on the boot code
- Load up
payload.bin(hekate - Nyx) bootloader5
Obviously the power glitching is the most interesting part. And as of today, the specific detail (hidden in the FPGA bitstream of the ICE40) is the only thing not open source. And probably one of the reasons why the modchip clones command such a high price6.
More details for most of these parts can be found by searching for appropriate keywords.
Closing words
If you are fascinated by the power glitching attack, then the Chip Whisperer toolkit as well as several papers (linked below) might be for you:
- Injecting Software Vulnerabilities with Voltage Glitching
- The Forgotten Threat of Voltage Glitching: A Case Study on Nvidia Tegra X2 SoCs
- Fault Injection Emulation for Systems in FPGAs: Tools, Techniques and Methodology, a Tutorial
-
Or possibly on the Nvidia Tegra X1 CPUs in general. ↩
-
And before you say digital downloads (of which we have more than fair share, too), how do you exactly wrap a digital download as a gift for our youngsters? The box has more appeal than an envelope with a redeem code. ↩
-
I remember first hearing about it in the context of PlayStation 2, but I wouldn’t be surprised if they went further back. :) ↩
-
To the best of my knowledge. ↩
-
And it continues from here to Atmosphère custom firmware. ↩
-
Around $120 shipped as of 2022-05-22. ↩